Setting a Group Tag During a Configuration Manager Task Sequence
In this post I’m going to talk about using the Windows autopilot deployment for existing devices Task sequence in configuration manager and modifying that task sequence to set a group tag during the process. You may know that traditionally this tasks sequence is used to ‘build’ devices and have them ready to start the autopilot process. I had a customer recently that had that very need. They had purchased a large number of machines that were delivered with Windows 10 installed and not Windows 11. As the customer was on their Windows 11 uplift journey already they were a bit disappointed to say the least and they opted to create a Configuration Manager task sequence to prep them for autopilot. That prep process was to include wiping the device and re-loading with Windows 11, adding the device to the tenants autopilot devices AND setting a group tag to drop the device into pre-created groups that control the apps and configurations the devices are going to receive during autopilot.
So… lets get started…
App Registration
The first thing you are going to need to create is an application registration. This app registration allows you to add devices to autopilot and set a group tag. We will work on the basis of least privilege and only allow the app registration a singular permission. The application registration will be called upon during out task sequence where we will pass our secret key to allow us to use it.
- Within the Microsoft Entra ID portal, navigate to App Registrations.
- Create a new Registration and name it as you see fit, in my case I called it “Autopilot GroupTag” you know, because I’m super inventive.


- You will now need to add the permission DeviceManagementServiceConfig.ReadWrite.All, as a Microsoft Graph Application Permission and grant consent.


- Finally you will need to create an application Secret and copy the secret key (Take note of the expiry date and set reminders for yourself and also, ensure to store the key safely)

Before continuing on you will need the following items:
- Your Directory (tenant) ID (Overview Blade of your app registration)
- The application (Client) ID (Overview Blade of your app registration)
- Your secret value (Certificates and Secrets Blade of your app registration)
Task Sequence
OK, lets now configure the task sequence. First create your autopilot task sequence following the Microsoft documentation from here.
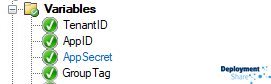
I wont regurgitate the task sequence configuration steps from the above documentation, however once you have the task sequence set up we’re going to make some adjustments. We are firstly going to create four variables

| TenantID AppID AppSecret GroupTag |
 |
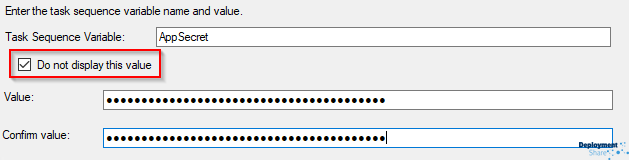
For the AppSecret, I strongly suggest you tick the box to “Do Not Display this Value”. This at least forms some sort of security for you as the secret is the key to the app registration and what it can do. Keeping that secure may or may not be important to you:
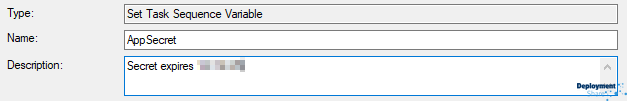
A description containing the expiry date might help in the event of failures too :-)
The Script
Next comes the fun bit. I lost a considerable amount of time testing this with numerous faults and errors. I was hoping that, I could use the Get-WindowsAuotpiloInfo script during the sequence to ‘just get it done’. But I ran into multiple issues. Namely, installing modules during WinPE because no matter what I tried, I was unable to leverage “Install-Module” correctly. The original script has some pre-req modules and so wouldn’t run without them present. This was causing me a headache. I then found the Recast Software community post (see references) where they used Invoke-Webrequest to pull in the module and then essentially move it to the correct location. This worked a treat.
Here is the script I used. Explanation below.
Info
Updated 21-07-2025 with new script logic and functions. Github script updated - Please check .VERSION section of the script header for more details.
Script available from my Github
*Click to drop down the box and reveal the script
<#PSScriptInfo
.VERSION 1.2.6
.AUTHOR
Jonathan Fallis - www.deploymentshare.com
Nick Benton - www.oddsandendpoints.co.uk
.RELEASENOTES
1.0.0 - Original
1.0.1 - Added Error Logging
1.0.2 - Updated to support Get-WindowsAutopilotInfoCommunity and empty groupTags
1.1.0 - Updated so the error handling works
1.2.0 - Improved logic
1.2.1 - Changed error handling to display in console and use transcript
1.2.2 - Added Microsoft.Graph.Authentication to the required modules and requirement for WinRM
1.2.3 - Changed WinRM configuration
1.2.4 - Updated logging settings
1.2.5 - Included diagnostics script to allow for troubleshooting
1.2.6 - Corrected params to match blog post images
PRIVATEDATA
#>
<#
.SYNOPSIS
Installs Get-WindowsAutopilotInfoCommunity.ps1 and calls it using the parameters
.DESCRIPTION
Used alongside a task sequence within Configuration Manager, this script was uses to add the device to autopilot and set a GroupTag
.EXAMPLE
.\Set-AutopilotGroupTag -TenantID "123456" -AppID "234567" -AppSecret "345678" -groupTag "AutopilotDevice"
.NOTES
Should use Task Sequence Variables for the parameters, e.g. %TenantID%, %AppID%, %AppSecret%, %GroupTag%
To allow data to be passed to SMSTSLog create a variable called 'OSDLogPowerShellParameters' and set it to 'True'
#>
param(
[Parameter(Mandatory = $true)]
[string]$TenantID,
[Parameter(Mandatory = $true)]
[string]$AppId,
[Parameter(Mandatory = $true)]
[string]$AppSecret,
[Parameter(Mandatory = $false)]
[string]$GroupTag
)
$ErrorActionPreference = 'stop'
$workingDir = "$env:SystemDrive\Windows\Temp"
$PowerShellDir = "$env:ProgramFiles\WindowsPowerShell\Modules"
$logFile = "$workingDir\Set-AutopilotGroupTag.log"
try {
Stop-Transcript | Out-Null
}
catch [System.InvalidOperationException]
{}
Start-Transcript -Path $logFile -Append
[System.Environment]::SetEnvironmentVariable('LOCALAPPDATA', "$env:SystemDrive\Windows\system32\config\systemprofile\AppData\Local")
#region connection check
if (Test-Connection 8.8.8.8 -Quiet) {
Write-Output 'Internet Connection OK'
}
else {
Write-Error 'Internet Connection check failed'
Stop-Transcript
exit 1
}
#endregion connection check
#region TLS1.2
try {
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
Write-Output 'Setting TLS1.2'
}
catch {
Write-Error "Setting TLS1.2 - $($_.Exception | Out-String)"
Stop-Transcript
exit 1
}
#endregion TLS1.2
#region Modules
$PowerShellModules = @('PackageManagement', 'PowerShellGet', 'Microsoft.Graph.Authentication')
foreach ($PowerShellModule in $PowerShellModules) {
$PowerShellModuleVer = switch ($PowerShellModule) {
PackageManagement { '1.4.8.1' }
PowerShellGet { '2.2.5' }
Microsoft.Graph.Authentication { '2.9.1' }
}
$PowerShellModuleURL = switch ($PowerShellModule) {
PackageManagement { "https://psg-prod-eastus.azureedge.net/packages/$($PowerShellModule.ToLower()).$PowerShellModuleVer.nupkg" }
PowerShellGet { "https://psg-prod-eastus.azureedge.net/packages/$($PowerShellModule.ToLower()).$PowerShellModuleVer.nupkg" }
Microsoft.Graph.Authentication { "https://psg-prod-eastus.azureedge.net/packages/$($PowerShellModule.ToLower()).$PowerShellModuleVer.nupkg" }
}
try {
if (!(Get-Module -Name $PowerShellModule)) {
$PowerShellModuleZip = "$workingDir\$PowerShellModule.$PowerShellModuleVer.zip"
$PowerShellModulePath = "$workingDir\$PowerShellModule\$PowerShellModuleVer"
$PowerShellModulePF = "$PowerShellDir\$PowerShellModule\$PowerShellModuleVer"
Write-Output "URL set to $PowerShellModuleURL"
Invoke-WebRequest -UseBasicParsing -Uri $PowerShellModuleURL -OutFile $PowerShellModuleZip
Write-Output "Downloaded PowerShellModule $PowerShellModule"
$Null = New-Item -Path "$PowerShellModulePath" -ItemType Directory -Force
Expand-Archive -Path $PowerShellModuleZip -DestinationPath "$PowerShellModulePath" -Force
Write-Output "Unzipped $PowerShellModule"
if (!(Test-Path -Path "$PowerShellDir\$PowerShellModule" -PathType Container)) {
$Null = New-Item -Path "$PowerShellDir\$PowerShellModule" -ItemType Directory
}
if (Test-Path -Path $PowerShellModulePF -PathType Container) {
Remove-Item -Path $PowerShellModulePF -Force -Recurse
Write-Output "Removed existing $PowerShellModulePF"
}
Move-Item -Path "$PowerShellModulePath" -Destination $PowerShellModulePF -Force
Write-Output "Moved $PowerShellModule to $PowerShellModulePF"
}
try {
Import-Module $PowerShellModule
Write-Output "$PowerShellModule Module Imported OK"
}
catch {
Write-Error "$PowerShellModule Import - $($_.Exception | Out-String)"
Stop-Transcript
exit 1
}
}
catch {
Write-Error "$PowerShellModule Module - $($_.Exception | Out-String)"
Stop-Transcript
exit 1
}
}
#endregion Modules
#region WinRM
try {
Set-WSManQuickConfig -Force -SkipNetworkProfileCheck
Write-Output 'Enabled WinRM'
}
catch {
Write-Error "WinRM - $($_.Exception | Out-String)"
Stop-Transcript
exit 1
}
#endregion WinRM
#region Windows Autopilot Info Community
try {
Install-Script Get-WindowsAutopilotInfoCommunity -Force
Write-Output 'Get-WindowsAutopilotInfoCommunity Installed OK'
try {
if (!$groupTag) {
$groupTag = ''
}
Get-WindowsAutopilotInfoCommunity -Online -tenantId $tenantId -appId $appId -appSecret $appSecret -groupTag $groupTag
Write-Output 'Get-WindowsAutopilotInfoCommunity executed successfully'
}
catch {
Write-Error "Get-WindowsAutopilotInfoCommunity execution - $($_.Exception | Out-String)"
Stop-Transcript
exit 1
}
}
catch {
Write-Error "Get-WindowsAutopilotInfoCommunity Install - $($_.Exception | Out-String)"
Stop-Transcript
exit 1
}
#endregion Windows Autopilot Info Community
#region Windows Diagnostics Community
try {
Install-Script Get-AutopilotDiagnosticsCommunity -Force
Write-Output 'Get-AutopilotDiagnosticsCommunity Installed OK'
exit 0
}
catch {
Write-Error "Get-AutopilotDiagnosticsCommunity Install - $($_.Exception | Out-String)"
Stop-Transcript
exit 0
}
#endregion Windows Diagnostics Community
- Thank you to Nick Benton for his input to the latest revision.
Script Step
Lets create a PowerShell Script step in our Task sequence.

We will opt to past a script into the step;

We will also configure the script to pass in four parameters.
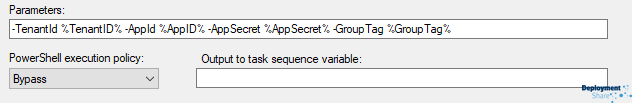
Notice that the script requires four parameters passing to it and would you believe it!? they match the task sequence variables we set up earlier. Wonderful. to reference a task sequence variable in a task sequence step you surround the text with “%” like in the above image.
Within the step you will notice the following;
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
This enables TLS 1.2. This is used to overcome networking issues experienced when attempting to go out to the www to receive content. There are then two sections which manually pull in the modules PowerShellGet and PackageManagement, both required to install the “Get-WindowsAutopilotInfo” script (which ensures the latest version is always pulled in) and to run it using the parameters we have passed in because… the script Get-WindowsAutopilotInfo uses the same parameter names we have passed in from our task sequence variables.
In testing I see the devices appear in Autopilot devices;

And then shortly after the device that is “Not Assigned” changes to pending, and lastly - assigned
And VOILA! Device present and accounted for.
Happy Customer.
Warning
05/12/2025 - It has been reported to me that, due to Microsoft introducing Graph throttling, a customer was having mixed results trying to use the task sequence on batches of machines (10 or more at a time). Please note this is out of my control. The script can be edited to add random wait times in to help mitigate this but as of yet this is untested.
Testing
Once testing begun there was an issue we noticed. Shift+F10 was not available in the event of a failure which was odd. This is controlled by the file C:\Windows\Setup\Scripts\DisableCMDRequest.TAG which we can remove with a simple Run Command Line Step.

Improvements / Ideas
- If you are not too scared about human-error, you could use something like ServiceUI to prompt the end user for text input to set the group tag and configure the variable GroupTag to the input of that.
- You could have a dynamic group tag set on hardware type using WMI queries. If you know a certain model requires a certain group tag you can set this condition on the Options tab of the task sequence variable step.
Your interest and support keep me motivated to create more content.
If you think others might benefit from this content, please consider sharing it
... Jonathan
Links and References
| Location | Link |
|---|---|
| Powershell is Fun | Upload Autopilot Hardware Hash |
| Recast Software | Enable PSGallery in a Task Sequence |
