Logon to Autopilot HAADJ Devices Using FortiClient VPN
I recently had a customer who uses FortiClient as their VPN solution, and they have recently embarked on setting up Hybrid AAD. We set their tenant up, sorted out licensing and I started to put in the fundamental elements to begin the journey to using Autopilot for provisioning devices. I had undertaken setting up AAD connect and using IDFix to remediate any issues, such as UPN suffixes for end-users via PowerShell, and we were ready to go. Equally, I had made them an Intune Win32app for FortiClient, and this installed and removed just fine using PSADT. I had already tested the Autopilot process and things were looking good.
Navigating to endpoint.microsoft.com and under “Windows Autopilot deployment profiles” I have two Hybrid Azure AD Joined profiles set up for the two scenarios my customer has unique to them. I have packaged up some apps (all using PSADT) and they have all been tested as working so I now want to run through the Autopilot process, have the apps install, join the machine to the domain using the Intune Connector and be faced with a login screen. I can only do this however if I use the optional feature (currently public preview at the time of writing this article) of “Skip AD Connectivity check (preview)”
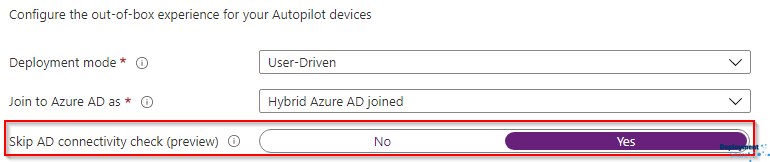
Essentially all this does is to ignore looking for a domain controller and continue through the rest of the autopilot process. Normally, its going to need to be able to see a domain controller to authenticate me for the first time and thus create me a local profile which, in future, I can use to log on to the machine, offline, should there not be a domain controller in sight. And so historically, it looks for one and bombs the Autopilot process if it doesn’t find one. This option will skip that check and let it run through right to the login page. Although remember, if you cant connect some sort of VPN or have that line-of-sight, you simply wont be able to log on with your domain credentials outside of the corporate network.
I tested this. It works. I cant log in.
So now I need to work on the FortiClient App which I intend to use to connect a VPN before logon. Its in Intune as a Win32 app so any configurations I need I should be able to just add to the script, redo the content and have it deploy. I need to ensure my settings are retained and deployed with the Intune app so I start digging around and trying to find out where they are stored.
I install a clean version of Fortinet Client (in my case its version 6.0.9) onto a test VM and I configure it to how I want it. I load up the client and select to unlock the settings first..
Then I proceed to untick what options I don’t require and making sure to tick the box for “Enable VPN before logon” (Vital!)
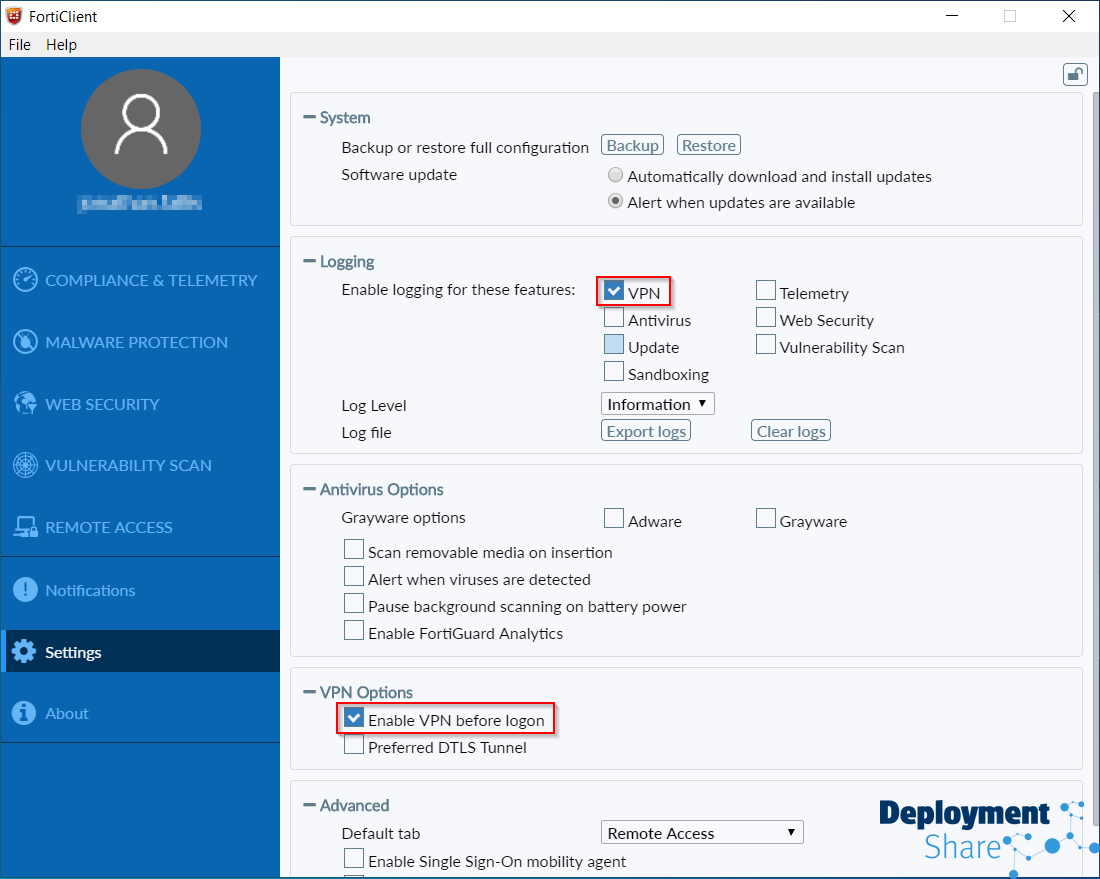
It is stated in the Microsoft Documentation that if your VPN solution supports connection before logon, then you should be able to make this work with any VPN solution. Previously there were named supported vendors. Worth noting.
Next we’re going to go to “Remote Access” and then “Configure VPN” to set up our base details for the VPN Connection
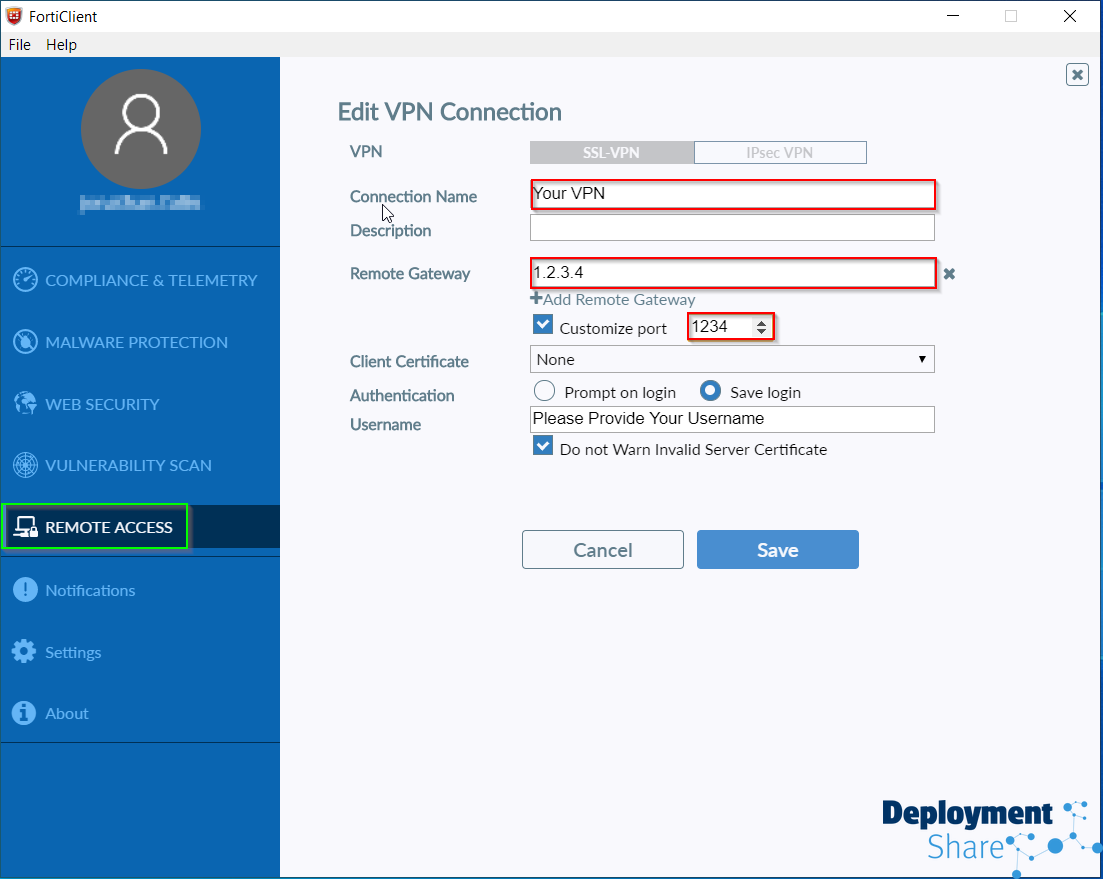
Then I’m going to configure my VPN, give it a name, the gateway IP and the port number. I just made up the below for illustration purposes so don’t shoot me if I cant use that port or that 1.2.3.4 isn’t a true IP address , you get the idea. I’m also going to leave “Prompt on login” selected rather than saving credentials.
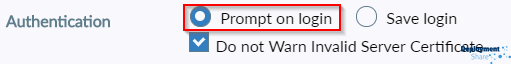
And finally hit save.
So we now have the basics configured.
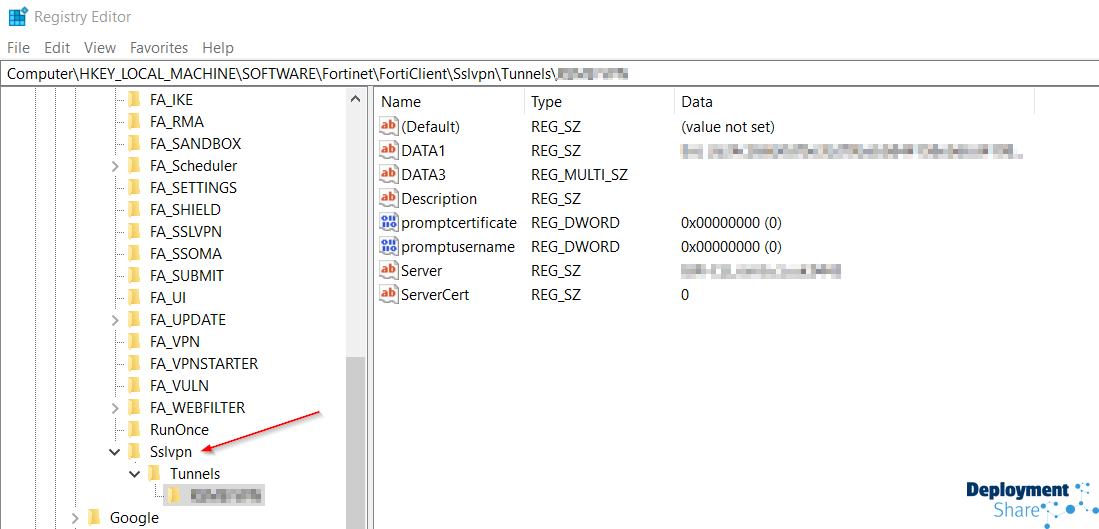
Next job was top somehow export that setup and have it deploy with the app deployed to the Autopilot profile. So I searched the registry and found where it was, the details are stored in HKEY_LOCAL_MACHINE\SOFTWARE\Fortinet\FortiClient\Sslvpn\Tunnels\My Test VPN
Great! So I export the key to a .reg file (the one pointed to in this image) and using my PSADT app I made I will add this during the “post-Installation” section.
Here is the code in my PSADT Script..
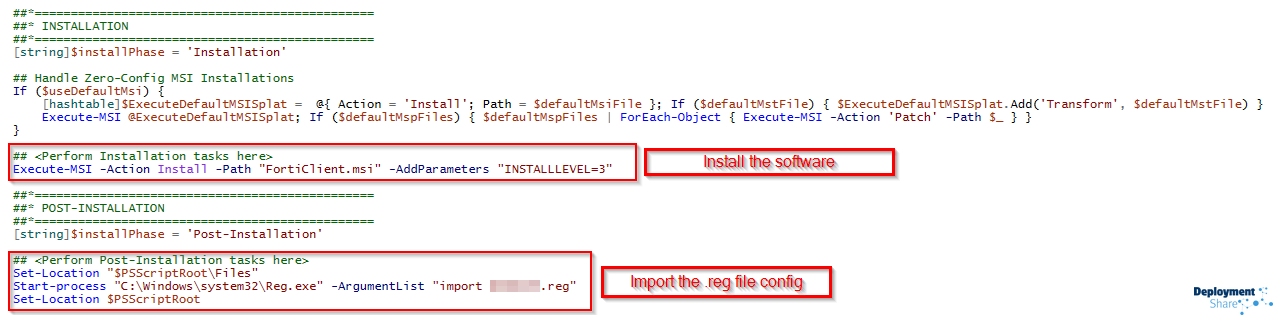
So essentially using the existing reg.exe to import the .reg file you exported. You could break this down and have the keys created with PowerShell, but I was lazy and used this method. There are a few ways this can improve, I’m sure.
I tested this with my PSADT script and it worked, so it now needs testing with Autopilot. I updated the Intune app content by creating a new .intunewin file and uploaded it ready to go. I added the app deployment where it needed to be and reset a laptop ready for the autopilot test. Next few pictures were taken from my phone so not the greatest. but here is the experience.
On the test device I added it to my network
I can see the Autopilot profile has pulled in and it requests I logon
Autopilot kicks off doing its thing…
OK, so now that’s finished I’m faced with a logon screen, first thing I do is click on sign on options
I can see here FortiClient has indeed installed during autopilot (WIN!)
I have to scroll down and untick the box for “Use my Windows credentials for VPN” because my username and password for the VPN is indeed, separate to my windows creds
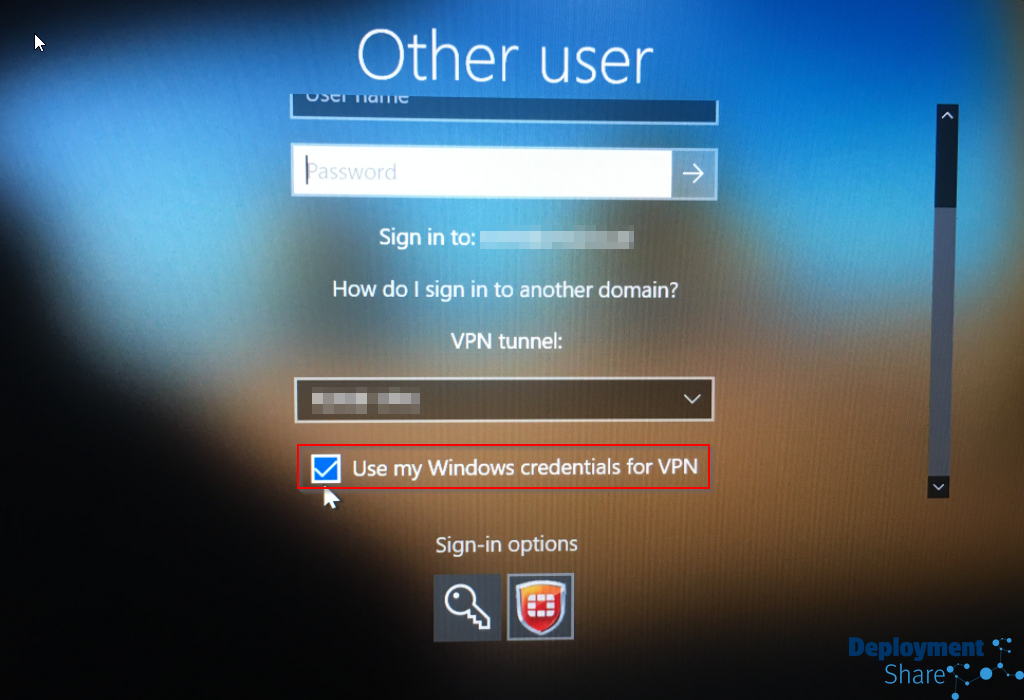
This opens up the creds box for the VPN
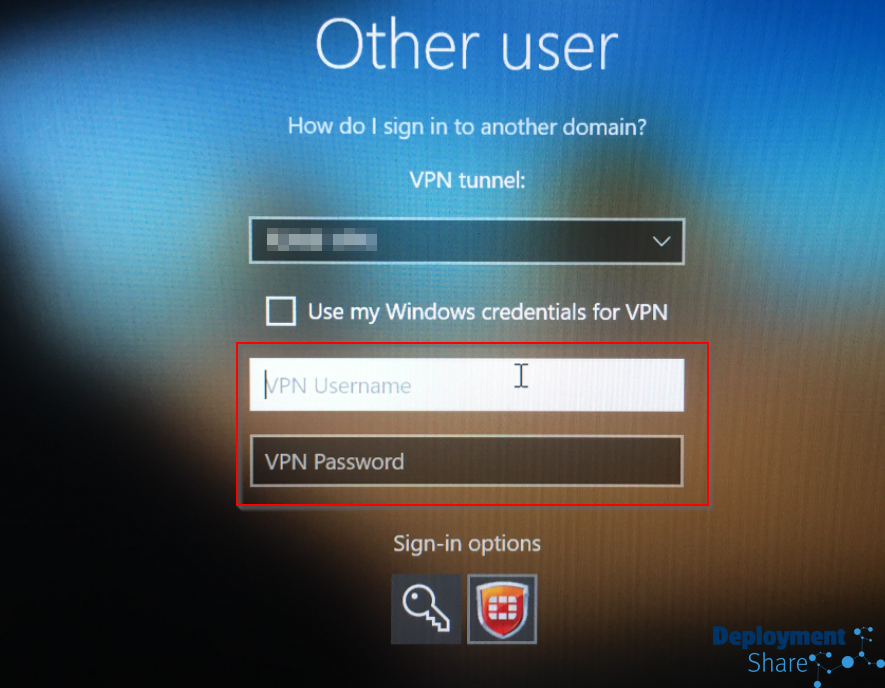
Then I scroll back up and input my windows credentials for my on prem domain account and attempt to log in (fingers crossed)
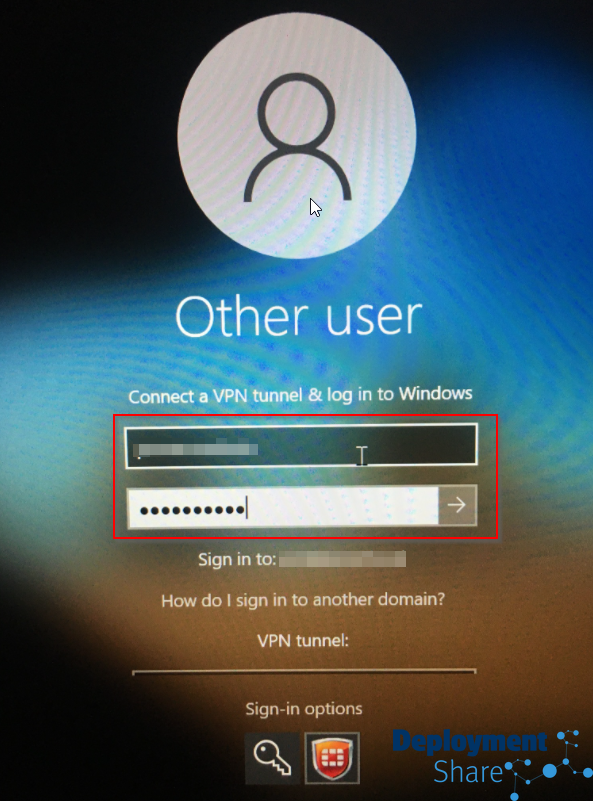
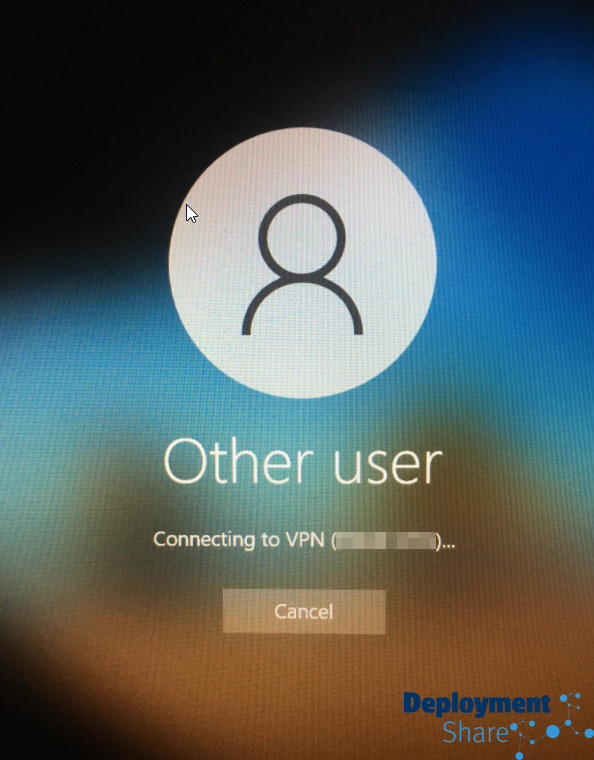
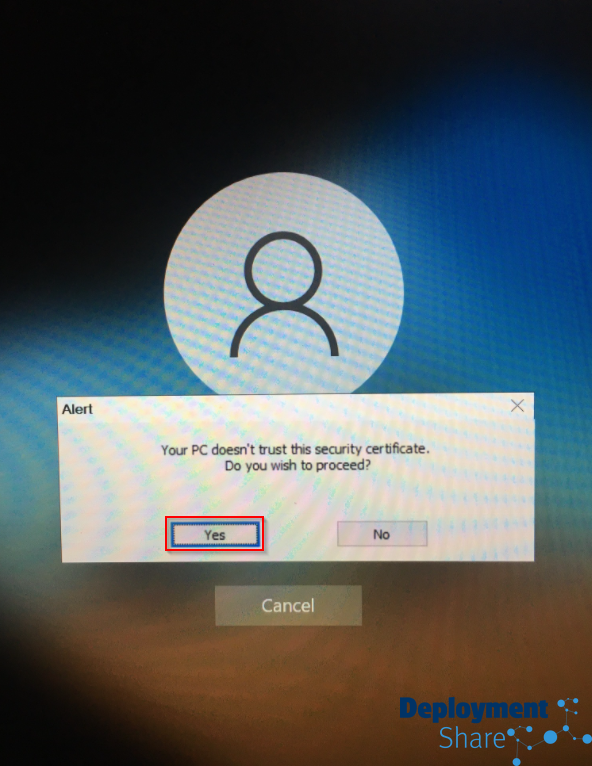
(I worked with the network provider to get the certificate on the machines during AP which stops this message but this is the message I got before I did this)
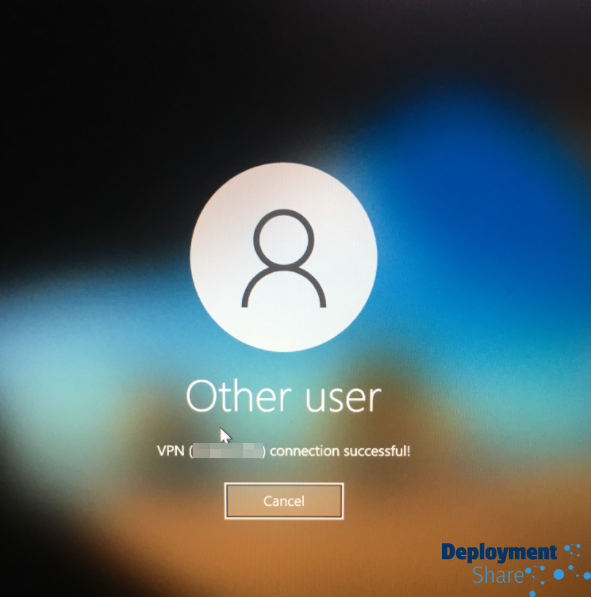
BIG WIN!!!
Aaaaand Boom….. I’m logged in.
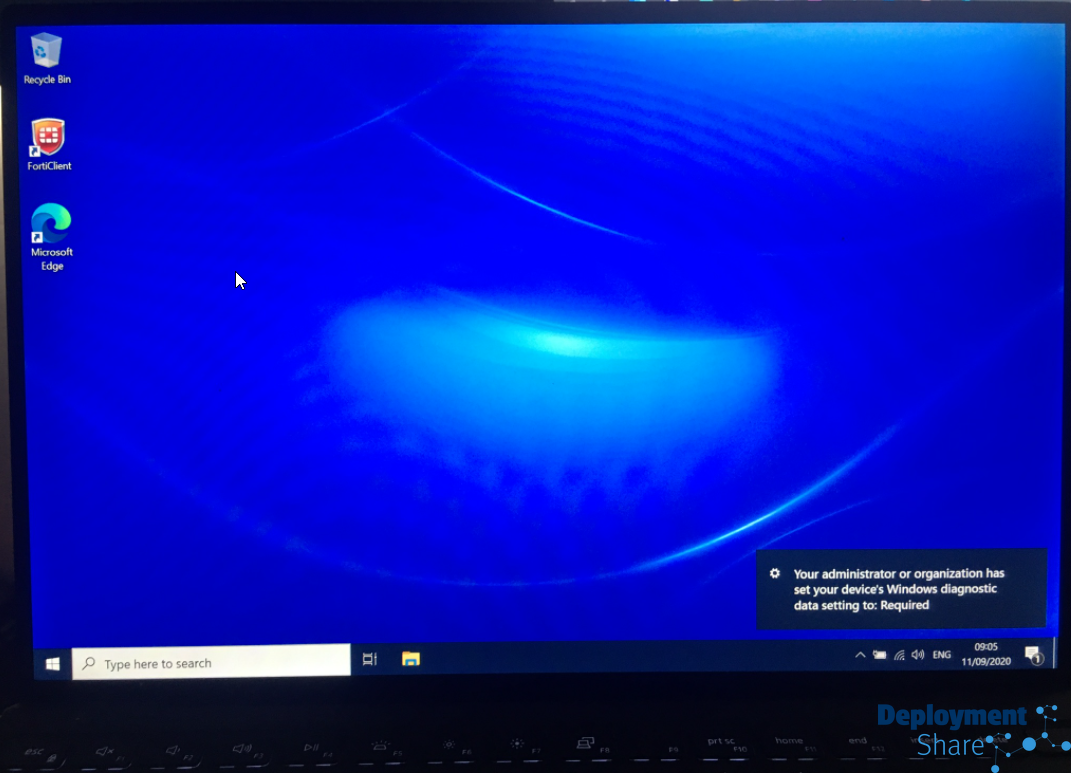
Very happy with this. What I would like you to take away from this blog post is that this methodology, in theory, could be used for any VPN provider. As long as you can export your profile and have it install with the client during Autopilot and it support connection before logon, this could be implemented for any VPN solution.
I would love to hear if you have got this working with any other VPN client
Thanks for reading
Jonathan.
